SSL Certificate
When deploying models on your own infrastructure, you may want to use your own SSL certificate or certificate chain for securing your model endpoint. However, as this certificate is not part the trusted root CA store, all request that try to access the model endpoint will fail. We can address this issue in two different ways:
Option 1: Register your SSL Certificate
To register your certificate, you can pass it as argument in the Advanced options when registering a new model :
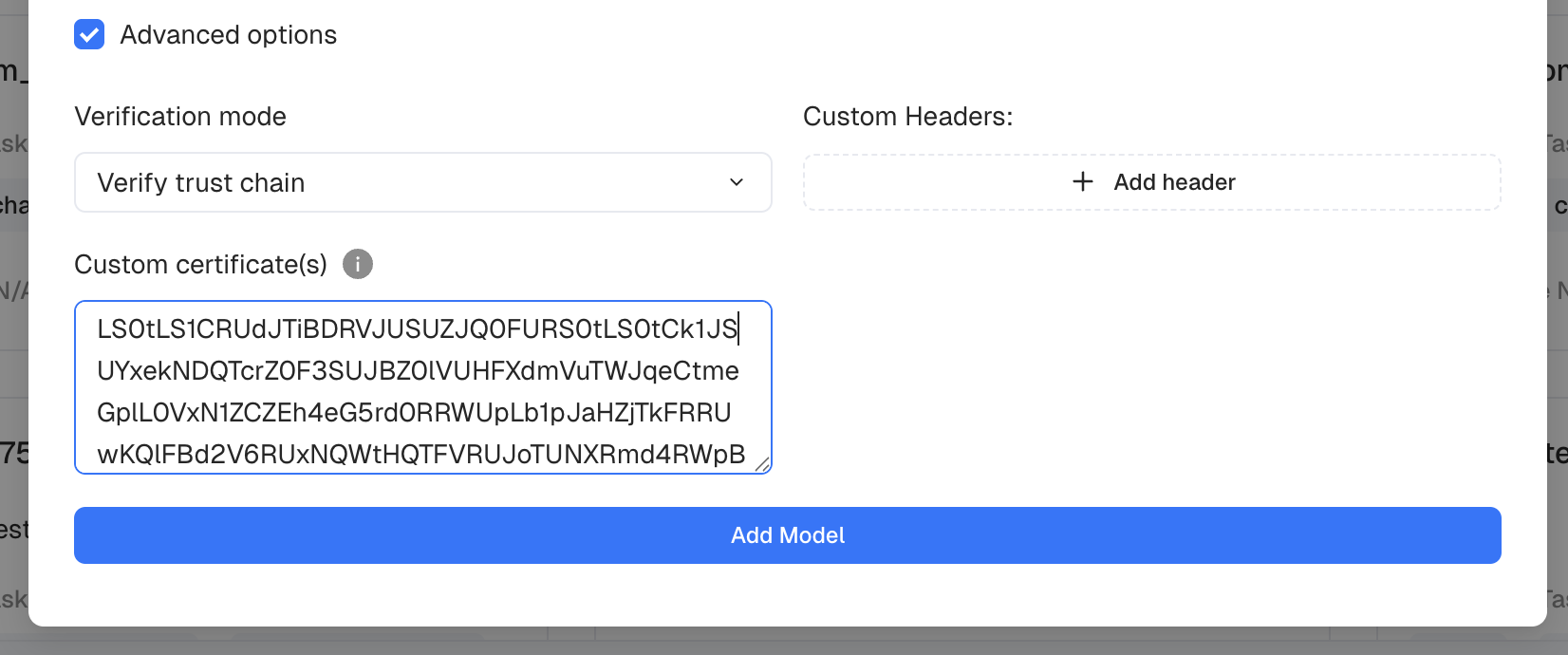
The value for trusted_ca must be a base64-encoded list of PEM certificates. If more than one certificate is given (e.g. if a certificate chain is used), the certificates must be listed as follows:
-----BEGIN CERTIFICATE-----
<CERT 1>
-----END CERTIFICATE----
-----BEGIN CERTIFICATE-----
<CERT 2>
-----END CERTIFICATE----One way to obtain such representation of your certificate(s) is by running cat cert.pem | base64 -w 0
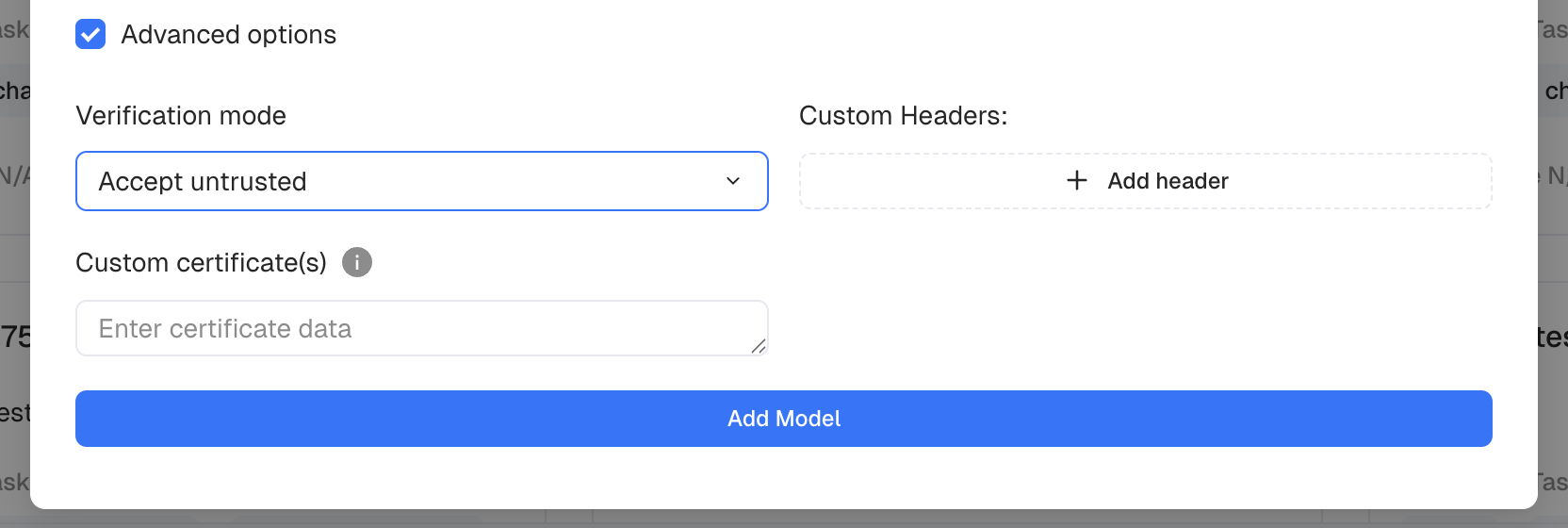
Option 2: Disable SSL Certificate Verification (Not Recommended)
Alternatively, if you are in a development environment and just need a quick fix, you can disable SSL certificate verification. To do so, register the model by selecting Accept untrusted verification mode:
Updated 9 days ago